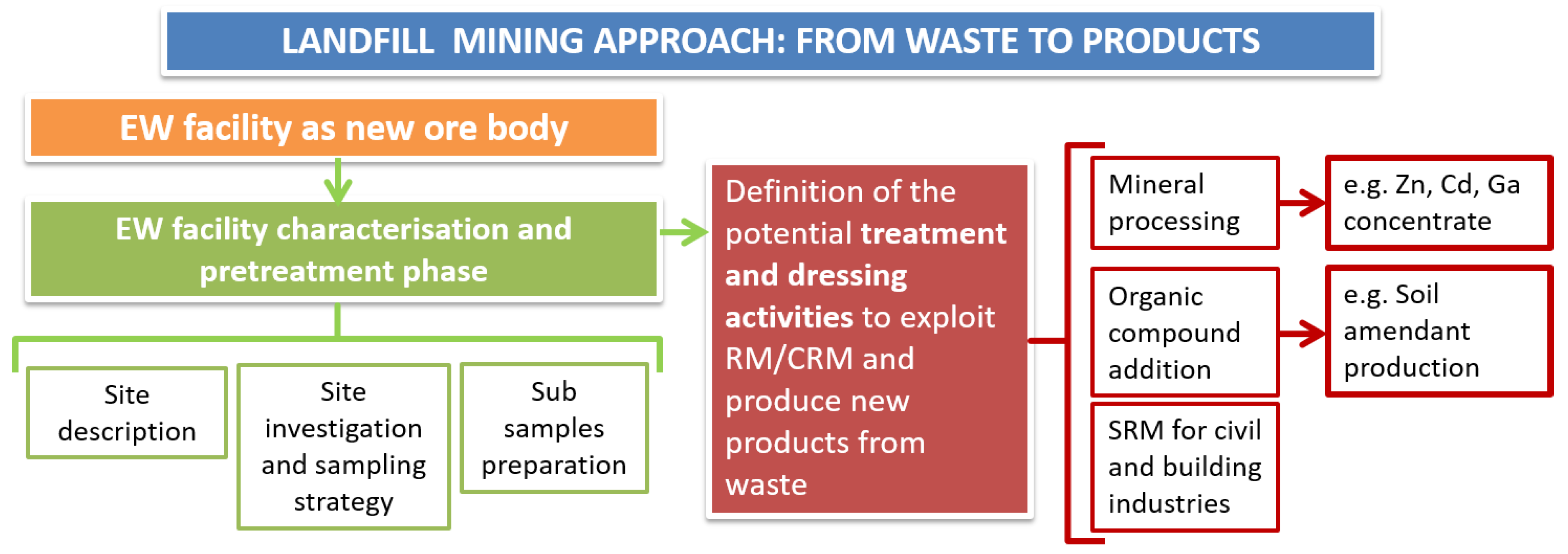
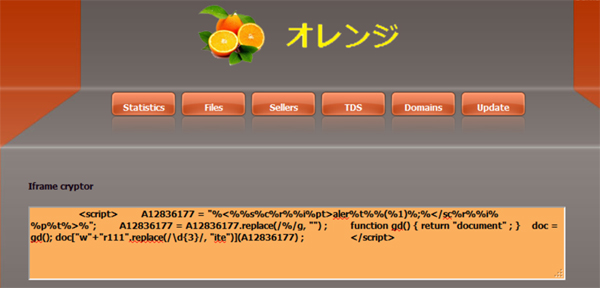
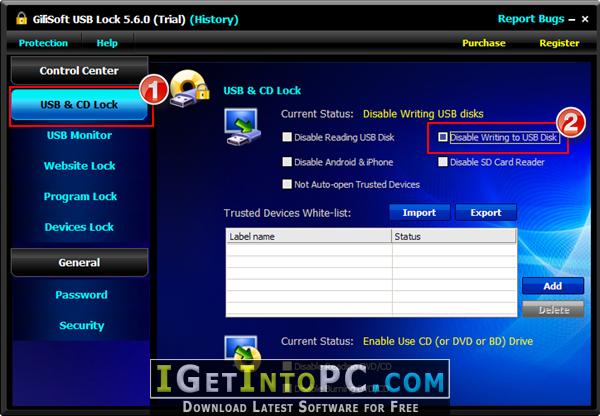
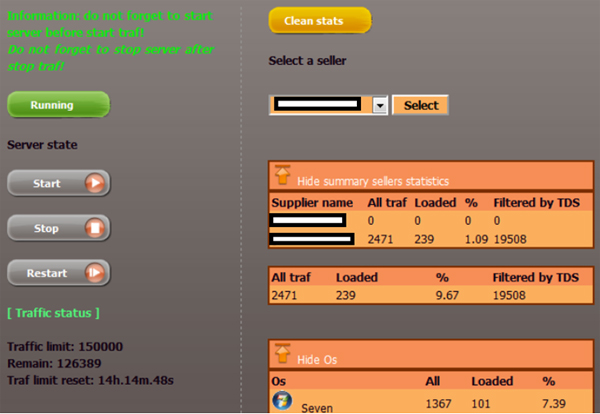
PDF) Responsible innovation by social entrepreneurs: an exploratory study of values integration in innovations
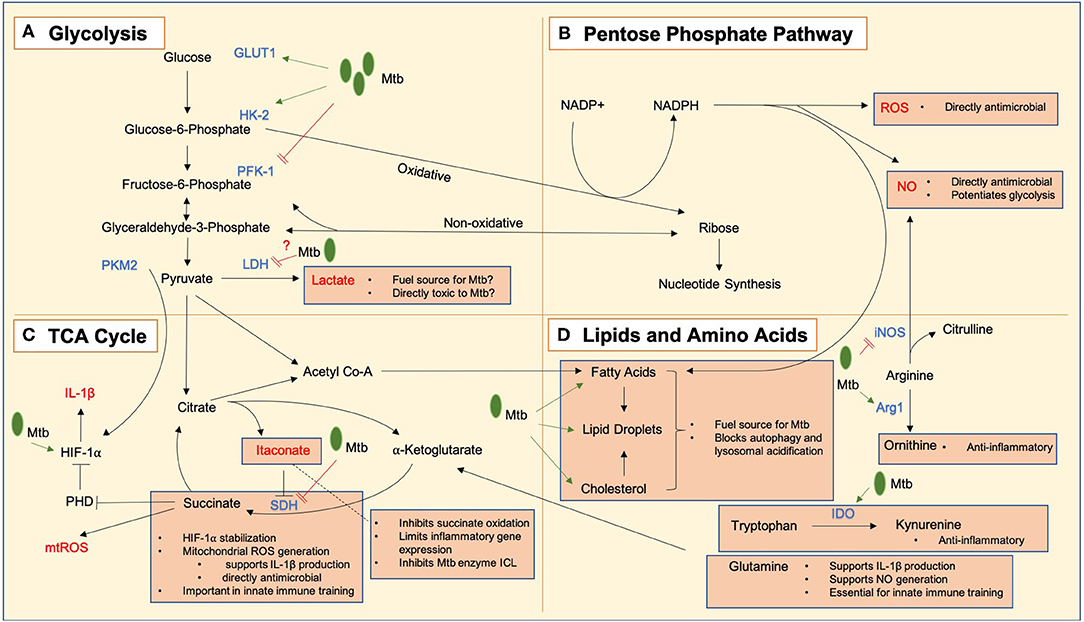
Frontiers | An Army Marches on Its Stomach: Metabolic Intermediates as Antimicrobial Mediators in Mycobacterium tuberculosis Infection | Cellular and Infection Microbiology

PDF) CHD3 helicase domain mutations cause a neurodevelopmental syndrome with macrocephaly and impaired speech and language

PDF) The carbohydrate-binding plant lectins and the non-peptidic antibiotic pradimicin A target the glycans of the coronavirus envelope glycoproteins